





Accept payments everywhere with Shift4's end-to-end commerce solution.
Supercharge your restaurant or bar with the latest point-of-sale, mobile, and contactless technology.
Food & BeverageProvide your guests a frictionless payment experience with Shift4's end-to-end hotel and travel solution.
Travel & HospitalityDeliver the ultimate fan experience with next-generation venue POS, mobile ordering, loyalty and more.
Sports & EntertainmentLaunch and grow your online business with our turnkey ecommerce platform or integrate to your existing site.
Turnkey eCommerceTake your online payments experience to the next level with our powerful developer platform.
Online PaymentsGet lucky with the end-to-end gaming solution that powers more than half the casinos on the Las Vegas strip.
Casinos & Online GamingStreamline checkout with the latest contactless payment technology and a complete omnichannel solution.
RetailFrom golf courses and ski resorts to gyms and education facilities, we have you covered.
SpecialtyEmpower your organization to do more good with our nonprofit donation solution – including crypto fundraising.
NonprofitsSimplify your payments operations with our end-to-end solution
Protect your customers’ data with ironclad security technology
Grow your business exponentially on our global commerce platform
Future-proof your business with the latest payment technology
Save money with the lowest total cost to accept payments
years in business
processed annually
current customers
technology integrations
annual transactions
payment methods
Shift4 handles every aspect of the commerce ecosystem to deliver a seamless, streamlined payments experience.
Give your business a competitive edge with mobile POS and contactless technology that deliver speed and convenience.
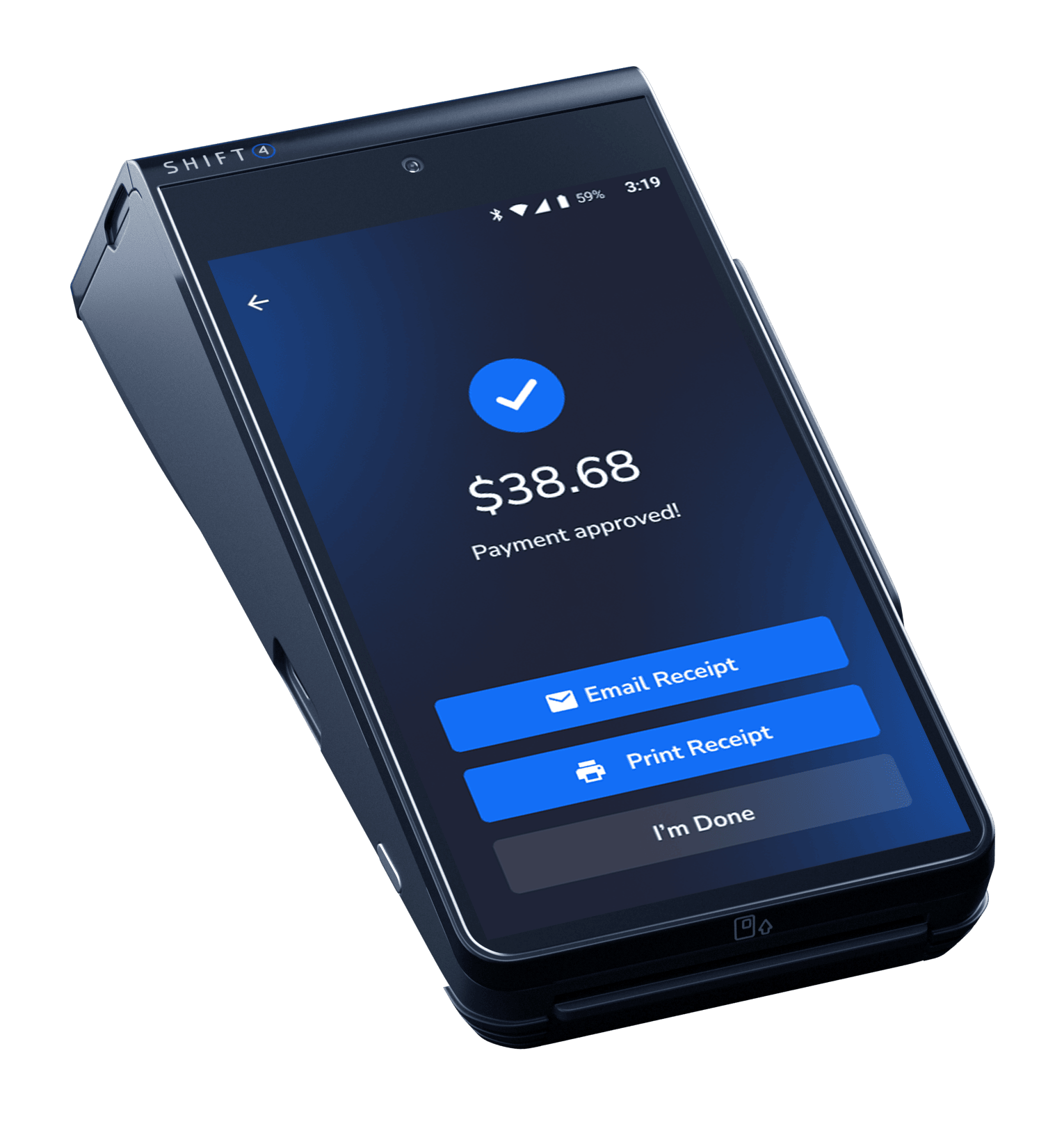
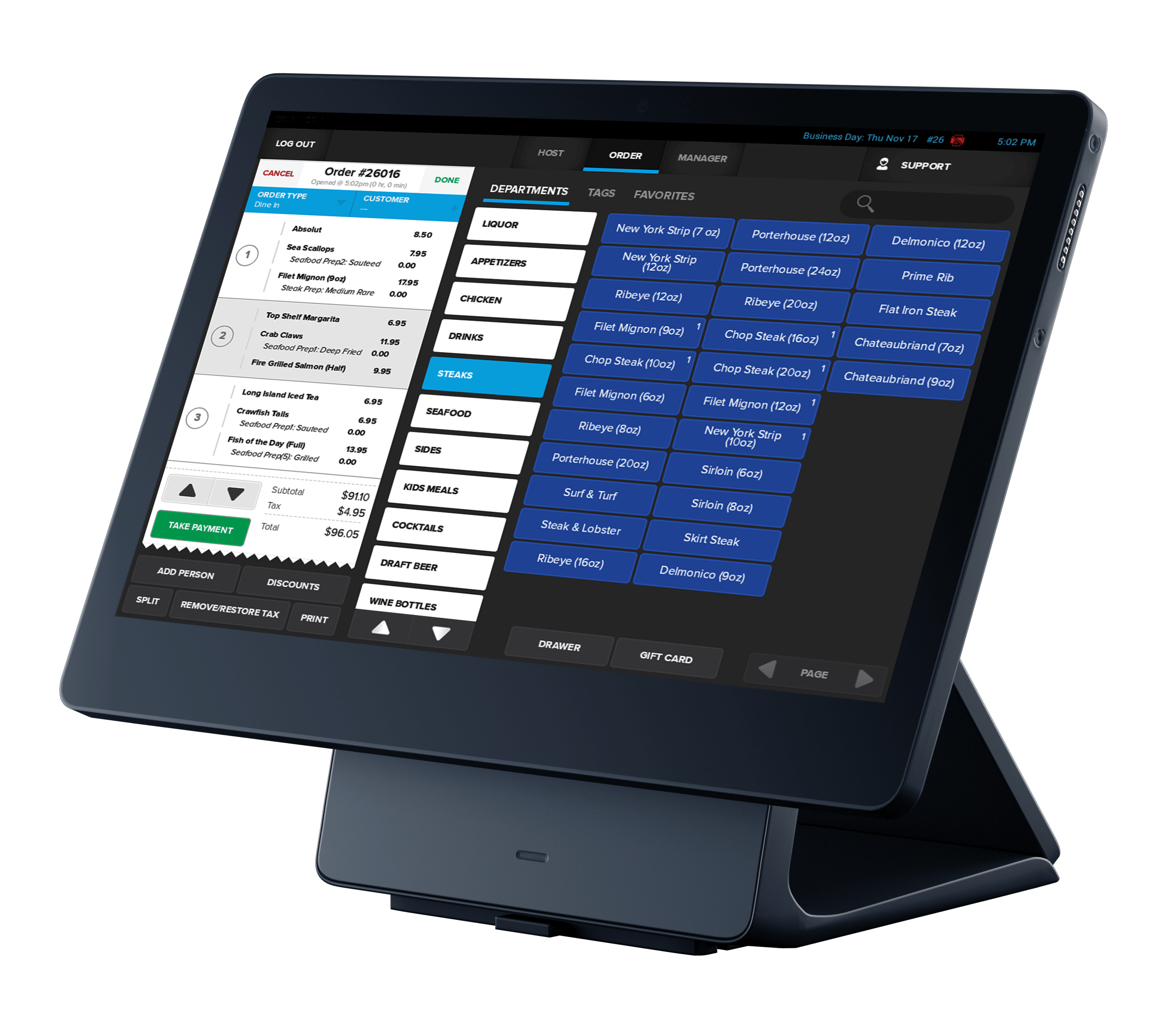
Streamline operations and future-proof your business with cutting-edge POS software and state-of-the-art hardware.
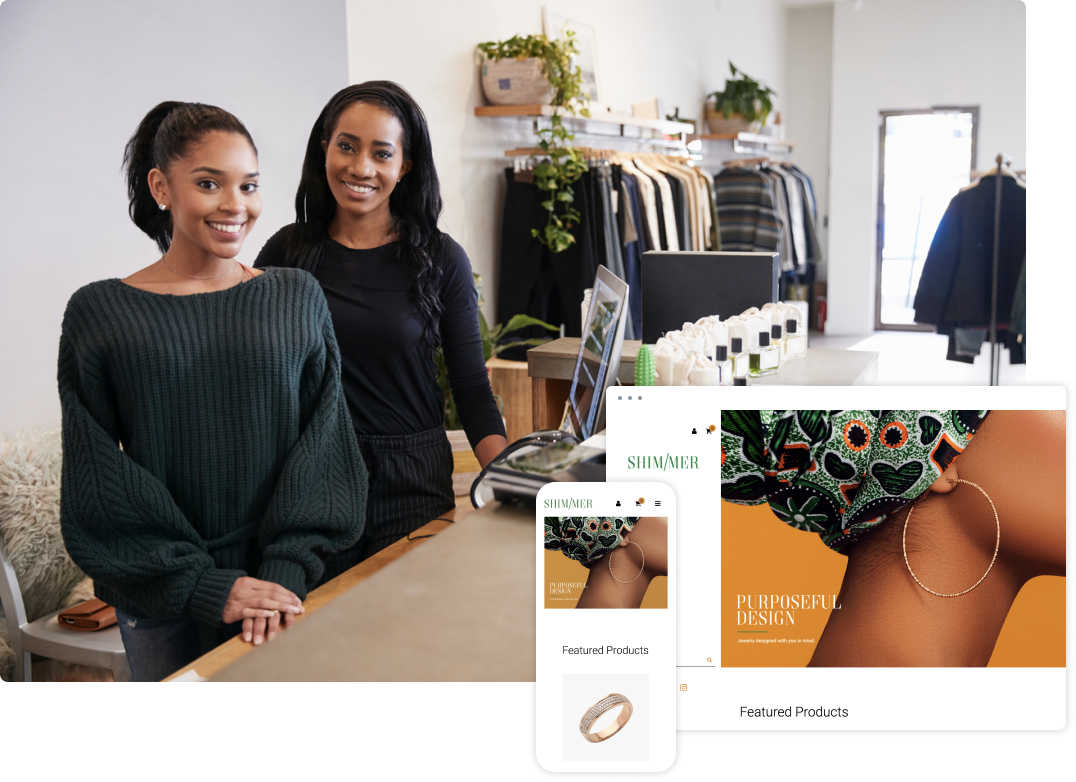
Deliver a frictionless online payment experience to boost your bottom line with custom tailored ecommerce solutions.
Make data-driven business decisions with enterprise reporting and actionable insights at your fingertips anytime, anywhere.
Not sure what you need? We’re here to answer all your questions.